基于“执行路径重建”的盗号木马逆向分析取证方法研究

Reverse Analysis into Stealing-information Trojan through “Reconstructing Execution Path”
基于“执行路径重建”的盗号木马逆向分析取证方法研究 |
徐国天 |
Reverse Analysis into Stealing-information Trojan through “Reconstructing Execution Path” |
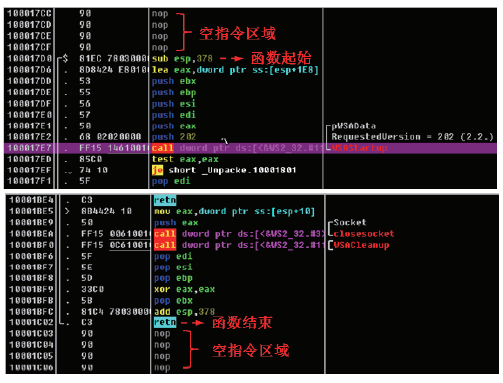
| 确定邮件发送函数的起始和结束位置 |
 |